Join our newsletter



"Cyberattacks no longer knock on the door; they slip through unnoticed. AI is the only way to detect and neutralize threats before they strike."
For decades, cybersecurity has been inherently reactive—waiting for attacks to occur before taking action. Traditional security systems rely on signatures, firewalls, and pre-defined rules, but modern cyber threats are dynamic, adaptive, and increasingly AI-driven themselves. Static defenses are no longer enough.
Enter AI-driven cybersecurity—a system that doesn’t just react but predicts, detects, and neutralizes cyber threats before they happen. AI models don’t rely on known attack signatures; instead, they analyze behavioral patterns, detect anomalies, and anticipate cybercriminal tactics before an exploit occurs.
Traditional security relies on predefined rules, but AI uses behavioral analysis to establish what “normal” looks like and immediately flags deviations.
AI doesn’t just analyze what has happened—it forecasts what could happen. By processing vast amounts of threat intelligence data, AI identifies patterns that indicate an imminent attack.
Manual threat hunting is time-consuming and requires extensive expertise. AI automates this process, scanning networks and endpoints for subtle indicators of compromise (IoCs) before they escalate.
Phishing attacks remain one of the most common cyber threats, yet traditional email security solutions often miss sophisticated attempts. AI leverages NLP to detect subtle linguistic patterns and social engineering tactics.
When an AI system detects an impending attack, it doesn’t just alert—it responds autonomously and in real-time.
💡 Cybercriminals are already using AI to design evasive malware, bypass authentication measures, and launch large-scale phishing campaigns. Companies that don’t embrace AI in their cybersecurity strategy are operating at a dangerous disadvantage.
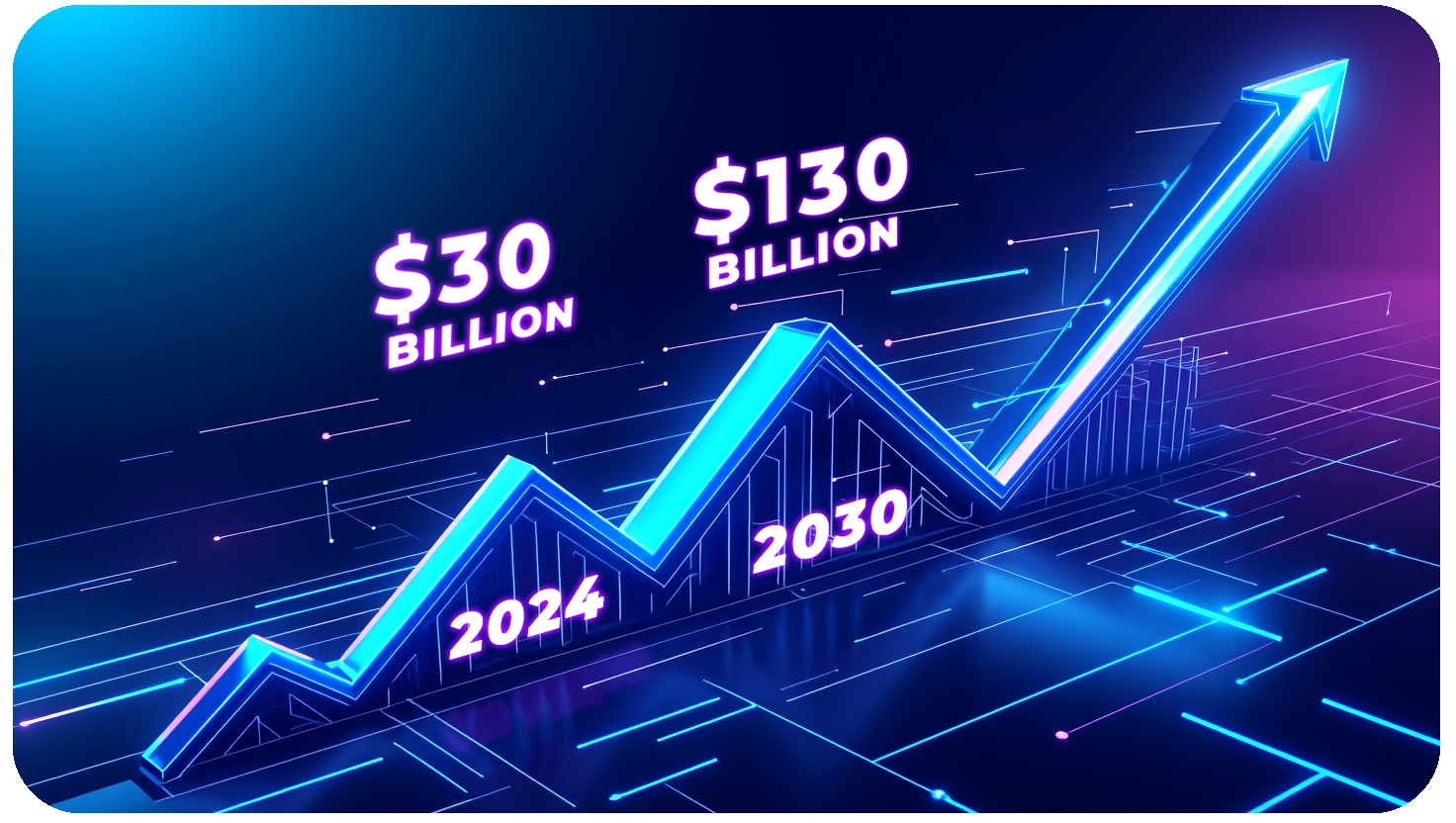
The AI cybersecurity market is not just growing; it’s exploding. From a $30 billion industry in 2024, it is expected to surpass $134 billion by 2030. This acceleration reflects the crucial role of AI in defending against advanced threats and its widespread adoption across the business sector.
At Kenility, we specialize in building AI-powered cybersecurity solutions tailored to businesses that can’t afford security gaps. Our expertise ensures proactive threat prevention, real-time monitoring, and automated risk mitigation—so you stay ahead of the attackers.
🔐 Is your organization prepared for AI-driven cyber threats? Let’s talk. Contact us at sales@kenility.com to future-proof your security.